Cashcow!
On this page
Challenge
Spending big on gifts is what I do, limits are not my problem!
Application: https://pizzamario2025.mendixctf.com
Difficulty: Medium
Solution
Solving this challenge begins with understanding the regular flow. This will tell us which protections we to bypass. Similar to the Gifts for me challenge we are looking at circumventing validations in the gift card order flow. The voucher code is already available when we create the order, but it cannot be claimed until it is committed. The commit is part of the confirm order, but that flow also performs the validation.
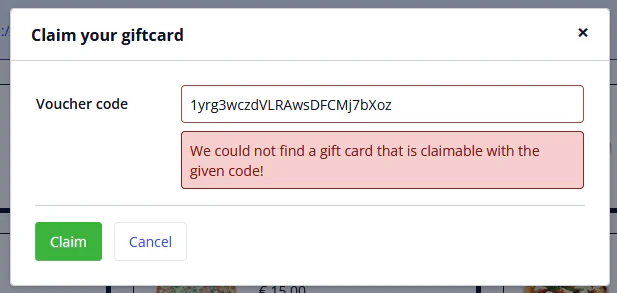
If we could only make the voucher code available by committing the object… Let’s create a gift card for €10.000,-, make a note of the voucher code and commit the object via the Client API. Then try to claim that voucher code, as it should be available in the database. Using the browser console we can identify the gift card object guid and use that in the Client API call to commit the object.
mx.data.get({
guid: "18858823440856359",
callback: function (obj) {
mx.data.commit({
mxobj: obj,
callback: function () {
console.log("done")
}
})
}
});Now enter the voucher code in the Claim your gift card pop-up and see what happens.
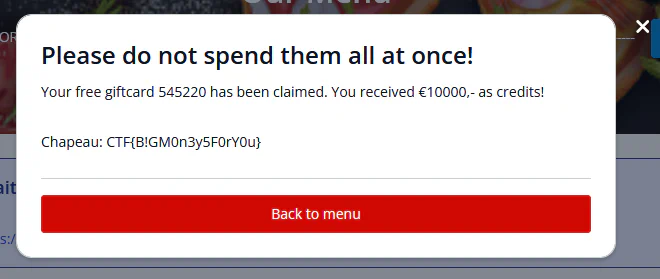
Mapping the normal flow and doing recon to understand developer intent is essential for exploitation.
Vulnerability
Validations —even when performed server-side— can be bypassed. Always enforce state and data integrity by revalidating critical conditions before processing or persisting data. This could map to TSU-03: Insecure microflows, but it also contributes to TSU-01: Insecure user roles or TSU-02: Insecure entity access. Make sure to setup strict entity access and roles which cannot bypass server-side validations and re-evaluate conditions when executing processes.
Flag
Control is an illusion.Flag
CTF{B!GM0n3y5F0rY0u}