eman ruoy esreveR
On this page
Challenge
,eman eht rettam on ,yletilop uoy teerg I .emas eht tca t’now I dna dnuora em pilf tuB ,thgis nialp ni eulc a sedih klaw uoy taht htap ehT .thgil eht ees noos ll’uoy ,yrrac uoy tahw trevnI ,garb ll’I terces ym ,yltcerroc em llaC .galf thguos-gnol ruoy dnif lliw uoy ereht dnA
After reversing the text:
I greet you politely, no matter the name, But flip me around and I won’t act the same. The path that you walk hides a clue in plain sight, Invert what you carry, you’ll soon see the light. Call me correctly, my secret I’ll brag, And there you will find your long-sought flag.
Application: https://pizzamario2025.mendixctf.com
Difficulty: Easy
Solution
The challenge hints that we must call something and then reverse a piece of text. Let’s approach this challenge step-by-step:
- Identify the target endpoint
In a previous challenge we discovered the exposed REST endpoint via rest-doc:
/couriers/eman/{eman}
Both the challenge and the endpoint contain the string “eman”, suggesting this is the service we need to call.
- Probe the endpoint
Supplying a dummy value (test) for {eman} yields the response:
Greetings from Wouter Penris @ Sopra Steria
The name Wouter Penris appears repeatedly throughout the application, it might be a clue.
- Apply the reversal
Using Wouter Pernis as input yields the same results. But the challenge explicitly asks us to reverse a text.
sirneP retuoW
The reversed name sirneP retuoW is accepted, and gives us the flag.
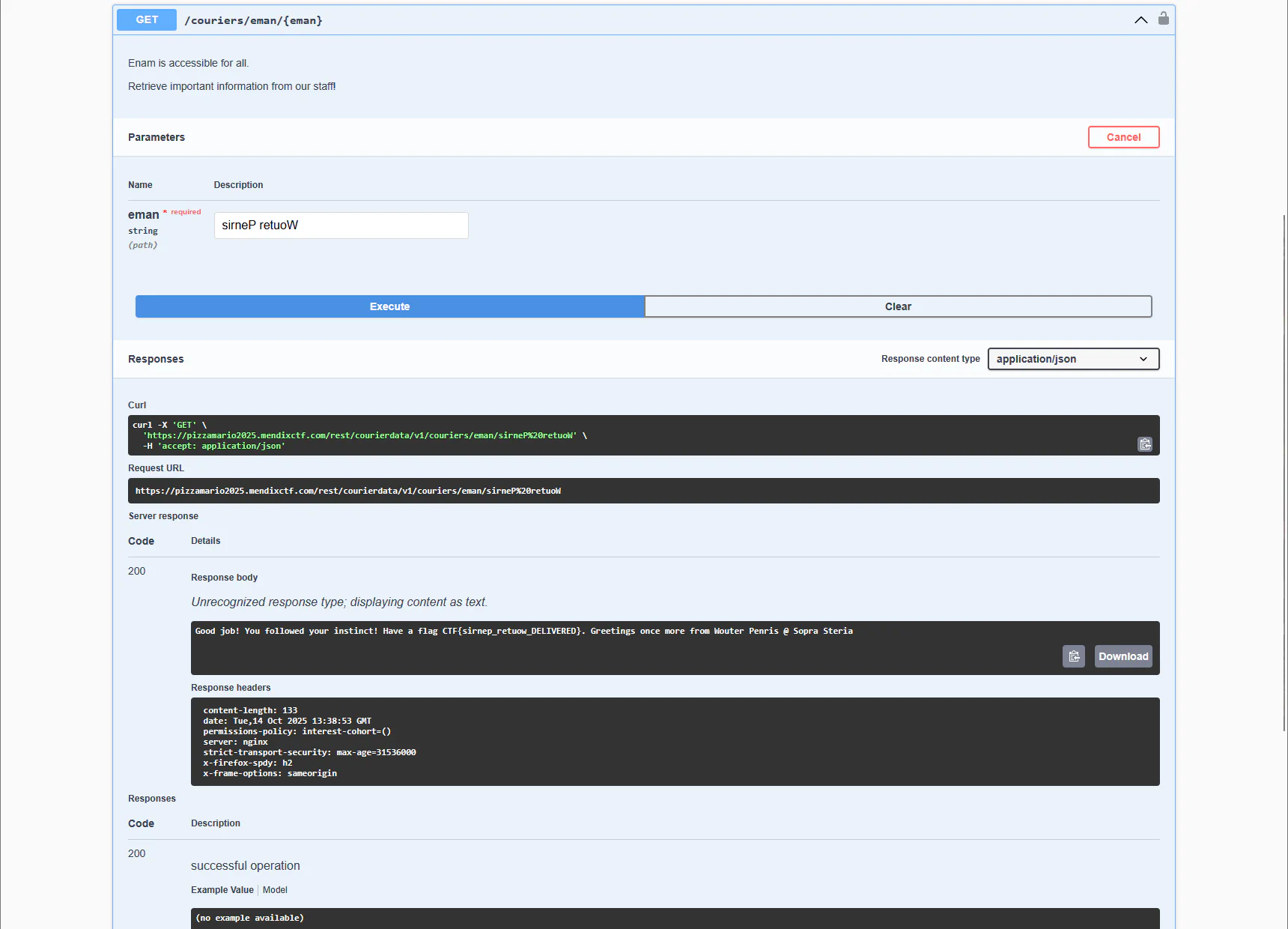
Good job! You followed your instinct! Have a flag CTF{sirnep_retuow_DELIVERED}. Greetings once more from Wouter Penris @ Sopra Steria
Vulnerability
While the challenge presents a creative scenario, such an exploit is unlikely to appear in real‑world applications. Nonetheless, it highlights two lessons:
- Security through obscurity fails – once an attacker learns the underlying system, its no longer secure
- Public integration endpoints (e.g., REST APIs) are prime attack surfaces because they often expose extensive data and are frequently misconfigured.
Flag
Never argue with the data.Flag
CTF{sirnep_retuow_DELIVERED}