AI will generate that for me
On this page
Challenge
Documentation is key, but given that I am lazy and our integrations are easy I will let my AI friend generate that.
Application: https://pizzamario2025.mendixctf.com
Difficulty: Easy
Solution
The description refers to integration documentation. Mendix offers various integration options (odata, rest, ws). For each option Mendix offers endpoints that can be used to obtain information about these services. The paths used by these endpoints end in -doc. Lets check whether they are disabled or if any of these endpoints are accessible.
Append /api-doc/, /ws-doc/, /rest-doc/, or /odata-doc/ to the base URL to quickly identify which documentation endpoints are exposed. These documentation endpoints enumerate published web and REST services and their operations, information an attacker can use to find potential attack surfaces. We can see that /rest-doc/ is exposed and contains documentation. It contains two REST services: CourierData and OAuthHandler.
Those who are familiar with the standard Swagger documentation will notice that the CourierData service contains something unusual: a reference to a PDF file.
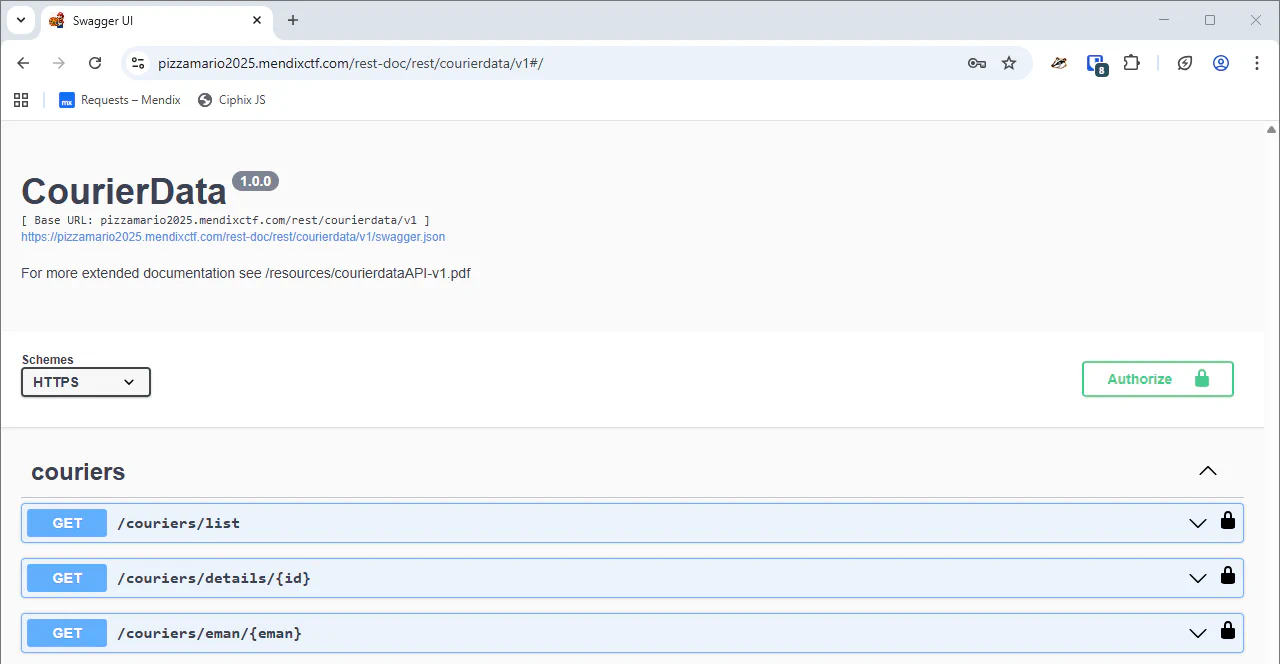
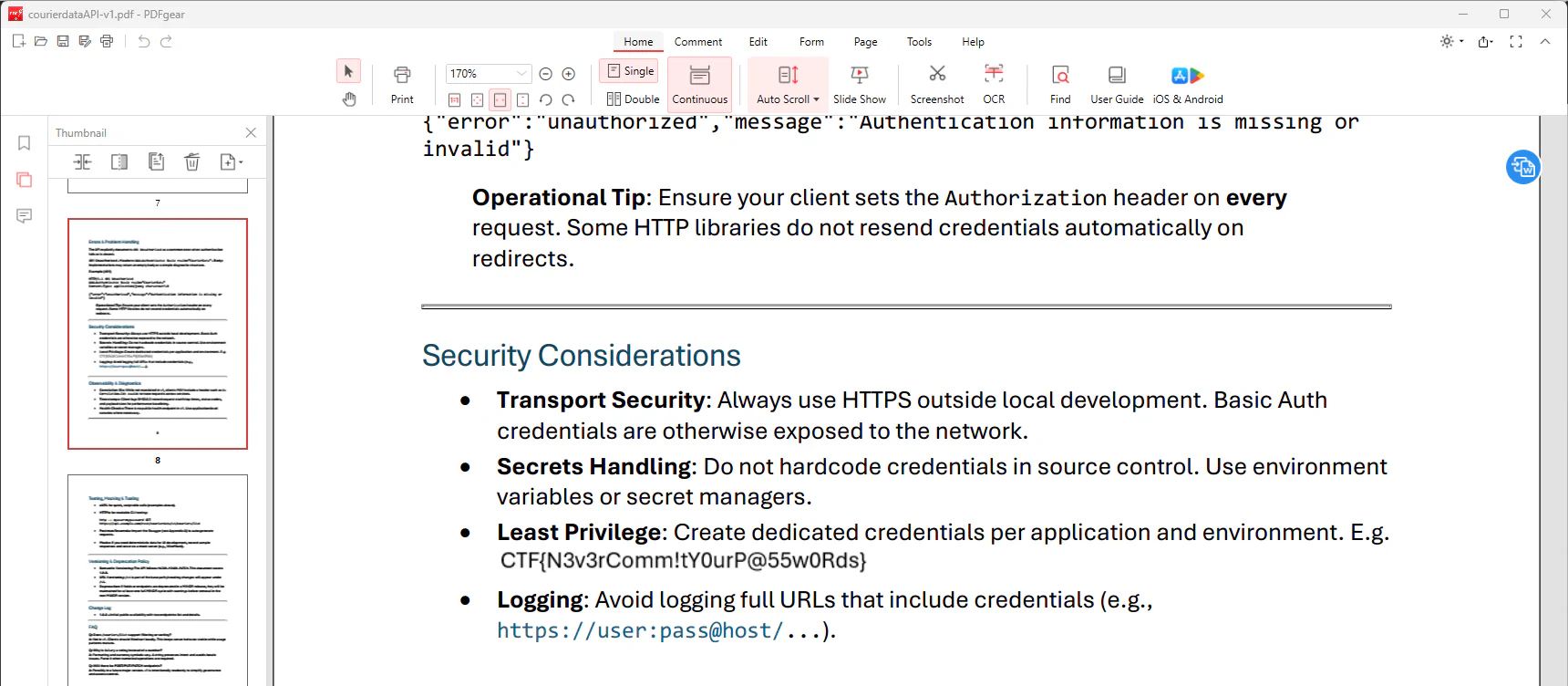
It’s quite an extensive PDF file, a quick CTRL+F search for CTF{ does not yield any results. But lets scan the contents, and there it is!
Vulnerability
Leaking secrets or exposing sensitive information can be mapped to TSU-04 Insecure published integrations of the S-Unit Top 10. As well as CWE-200: Exposure of Sensitive Information to an Unauthorized Actor
Flag
A wild CTF flag appears!Flag
CTF{N3v3rComm!tY0urP@55w0Rds}